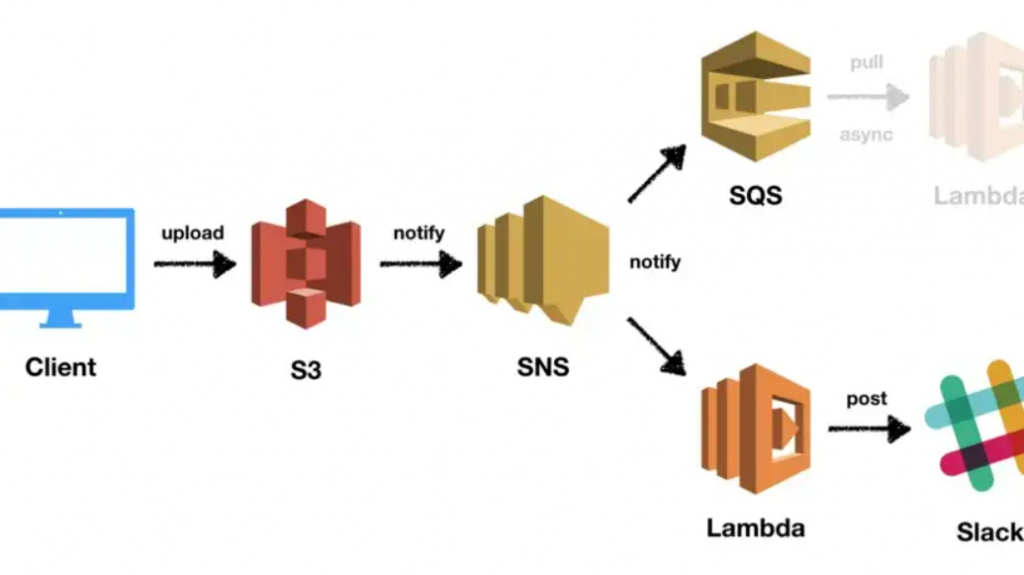
Introduction to securing Amazon Notification Service (SNS)
Amazon Simple Notification Service (SNS) is a fully managed, scalable messaging service that enables you to send notifications to endpoints such as mobile devices, email addresses, and other services. While SNS is a highly secure and reliable service, there are potential threat scenarios that you should be aware of and take steps to mitigate.
Securing Amazon Simple Notification Service (SNS) is important for several reasons. First, SNS is a critical component of many cloud-based applications and services, and securing it can help ensure the reliability and availability of these applications. For example, if an attacker is able to gain access to an SNS topic or subscription, they could potentially send malicious messages to endpoints or even delete the topic or subscription altogether, disrupting the operation of the underlying application.
Second, SNS is often used to send sensitive information, such as user notifications or alerts. If this information is not properly secured, it could be accessed by unauthorized users, potentially leading to data breaches or other security incidents. By implementing security measures for SNS, you can help protect the confidentiality and integrity of the information sent through the service.
Third, SNS is a fully managed service provided by Amazon Web Services (AWS), and as such, it is subject to the same security standards and compliance requirements as other AWS services. This means that securing SNS is not only important for the security of your own applications and data but it is also required to meet the security and compliance requirements of AWS.
Threat modelling AWS SNS
Threat modelling is the process of identifying, analyzing, and mitigating potential security threats to a system or application. In the context of Amazon Simple Notification Service (SNS), potential threat scenarios could include unauthorized access to SNS topics and subscriptions, the use of SNS for spamming or phishing, and the use of SNS for denial of service (DoS) attacks.
To properly threat model SNS, you should first identify the potential threats to your SNS implementation. This could include external threats, such as attackers attempting to gain unauthorized access to your SNS resources, as well as internal threats, such as authorized users misusing the service.
Next, you should analyze the potential impact of each threat on your SNS implementation. This could include the loss of confidentiality, integrity, or availability of your SNS resources, as well as the potential financial or reputational impact on your organization.
Finally, you should implement appropriate measures to mitigate the identified threats. This could include implementing strict access controls, using SNS message attributes to filter and block suspicious messages, monitoring your SNS usage, and using encryption to protect the confidentiality of your messages.
AWS SNS Threat scenarios
- One potential threat scenario for using SNS is unauthorized access to your SNS topic or subscription. If an attacker is able to gain access to your SNS topic or subscription, they could potentially send malicious messages to your endpoints or even delete your topic or subscription altogether. To prevent this, you should implement strict access controls for your SNS resources, including using IAM policies to limit who has access to your SNS topics and subscriptions. You should also regularly monitor your SNS resources for any unauthorized access or activity.
- Another potential threat scenario is the use of SNS for spamming or phishing. If an attacker is able to create an SNS topic or subscription and send messages to large numbers of endpoints, they could potentially use this to send spam or phishing emails to your users. To prevent this, you should implement controls to prevent the creation of large numbers of SNS topics or subscriptions, and monitor your SNS messages for any spam or phishing content. You can also use SNS message attributes to filter and block messages that contain suspicious content.
- A third potential threat scenario is the use of SNS for denial of service (DoS) attacks. If an attacker is able to send large numbers of messages to an SNS topic, they could potentially overwhelm the service and cause it to become unavailable to other users. To prevent this, you should monitor your SNS usage and implement throttling controls to limit the number of messages that can be sent to a single SNS topic. You can also use Amazon CloudWatch alarms to monitor for sudden spikes in SNS usage and take action if necessary.
Securing AWS Simple Notification Service (SNS)
Here are some recommended steps for securing Amazon Simple Notification Service (SNS) with links to relevant sources and industry best practices:
- Implement strict access controls for your SNS resources, including using IAM policies to limit who has access to your SNS topics and subscriptions. You can find more information on using IAM policies for SNS in the AWS documentation here: https://docs.aws.amazon.com/sns/latest/dg/access-control-policy-language.html
- Use SNS message attributes to filter and block messages that contain suspicious content, such as spam or phishing attempts. You can find more information on using message attributes in the AWS documentation here: https://docs.aws.amazon.com/sns/latest/dg/message-attributes.html
- Monitor your SNS usage and implement throttling controls to limit the number of messages that can be sent to a single SNS topic. This will help prevent misuse of the service and protect against denial of service (DoS) attacks. You can find more information on using throttling controls in the AWS documentation here: https://docs.aws.amazon.com/sns/latest/dg/sns-throttling.html
- Use Amazon CloudWatch alarms to monitor for sudden spikes in SNS usage and take action if necessary. This will help you detect and respond to potential security incidents in real-time. You can find more information on using CloudWatch alarms in the AWS documentation here: https://docs.aws.amazon.com/AmazonCloudWatch/latest/monitoring/AlarmThatSendsEmail.html
- Regularly monitor your SNS resources for any unauthorized access or activity. This will help you identify and respond to potential security threats in a timely manner. You can find more information on monitoring SNS in the AWS documentation here: https://docs.aws.amazon.com/sns/latest/dg/monitoring-using-cloudwatch.html
- Consider using encryption for your SNS messages, either through the use of Amazon SNS encryption or by implementing your own encryption solution. This will help protect the confidentiality of your messages and ensure that only authorized users can access them. You can find more information on using encryption with SNS in the AWS documentation here: https://docs.aws.amazon.com/sns/latest/dg/sns-encrypt-decrypt-messages.html
- Follow the latest security best practices and guidelines from AWS when using SNS, and regularly review and update your security measures to ensure they are up-to-date and effective. You can find more information on security best practices for SNS in the AWS Security Best Practices whitepaper here: https://d1.awsstatic.com/whitepapers/Security/AWS_Security_Best_Practices.pdf
In summary, there are several potential threat scenarios for using SNS, including unauthorized access, spamming and phishing, and DoS attacks. To mitigate these threats, you should implement strict access controls, monitor your SNS resources for any suspicious activity, and implement throttling controls to prevent the misuse of the service. By following these best practices, you can help ensure the security and reliability of your SNS implementation.