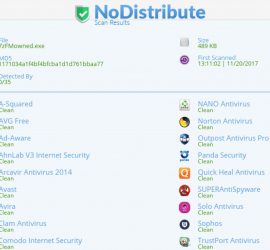
Introduction During Penetration testing engagement you are required backdooring PE file with your own shellcode without increasing the size of the executable or altering its intended functionality and hopefully making it undetectable (UD) how would you do it?. For example, after recon, you gather information that a lot number of employees use a certain “program/software”. The social engineering way to get in the victim’s network would be a phishing email to employees with a link to download “Updated version of that program”, which actually is the backdoored binary of the updated program. This post will cover how to backdoor a […]
Binary Exploitation
1 post