Amazon Web Services (AWS) Lambda is a popular serverless computing platform that allows users to run code without the need to manage infrastructure. While it offers many benefits, like scalability and low costs, it also comes with some potential security threats that you should be aware of and take steps to mitigate. Security is important to AWS Lambda for several reasons. First, Lambda functions often process sensitive data, such as customer information, financial records, and personal data. If this data were to be accessed or modified by unauthorized parties, it could result in serious harm to individuals and businesses. Therefore, […]
Haider Mahmood
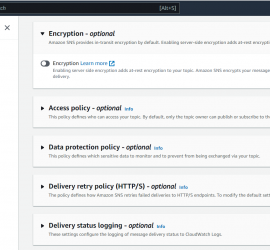
Introduction to securing Amazon Notification Service (SNS) Amazon Simple Notification Service (SNS) is a fully managed, scalable messaging service that enables you to send notifications to endpoints such as mobile devices, email addresses, and other services. While SNS is a highly secure and reliable service, there are potential threat scenarios that you should be aware of and take steps to mitigate. Securing Amazon Simple Notification Service (SNS) is important for several reasons. First, SNS is a critical component of many cloud-based applications and services, and securing it can help ensure the reliability and availability of these applications. For example, if […]
Introduction I have been doing Bug bounties for over 8 years now as a researcher on different platforms (Hackerone, Bugcrowd, Synack etc) but recently I had recent experience in bug bounties from the other side of the table, from the program side. After conducting the feature assessment and POCs of major platforms (an activity spanning over three months) I would like to share my experience which would hopefully help you choose the “right” platform to achieve your bounty objectives. This Bug Bounty Platform Comparison post focuses on why you need a bug bounty platform, criteria, and considerations in choosing the […]
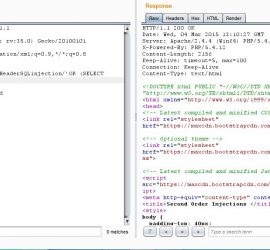
Introduction This post is the second in a series of noob-friendly posts that I am doing on SQL injection. Earlier I explained Second Order SQL Injections with Example. So in this post, I will be explaining the HTTP header Blind SQL injection, I prepared a Demo for the HTTP header Blind SQL injection For Example, HTTP has many reserved header fields the header I am choosing for the demonstration is the referrer header. What is HTTP Referrer Header? A referrer header is an HTTP header field, it’s simple job is to identify where the request originated from, for example, if […]
Introduction Organizations in today’s digital world hold data of their customers and clients which makes them a target for hackers, Organisations must follow robust cyber security policies/standards/guidelines to protect themselves, their employees, and most importantly their data against a wide range of threats. A Information security checklist helps organizations keep a track of their cyber security health to make sure an attacker cannot get unauthorized access to information that is stored on devices such as servers, databases, cloud, workstations, etc. Cyber incidents are on the rise, organisations are continuously attacked by threat actors that can range from lone wolfs to […]
STRIDE Threat modelling Which THREAT modelling framework/methodology should I go for? This is a very common question nowadays, since the “Shift-left revolution”, we have all been trying to introduce security as early into the SDLC as possible (if we aren’t? we should!). THREAT modelling is the foundational activity of shifting left, which basically means finding threats early into the SDLC. Finding threats early in the software development lifecycle helps you save costs in terms of time, finances and more importantly possible reputational damage. Now that you are sold on doing threat modelling in the design phase of SDLC, the question […]
I recently passed the CISSP exam! This post is about my journey to CISSP, Why I choose to do it, the study material I used and how I prepared for the exam. Why? In my university days, I started doing freelance penetration testing, bug bounties and then joined a company where I used to do on-site penetration testing for clients. Over the years I realized that penetration testing as a field is getting saturated and shrinking because of a number of reasons, for example, introduction of framework based applications running on cloud-based architecture means my penetration testing skills are down […]
Its been 2 years and 8 months I was working as a Penetration tester looking after application security for the most part of my day. As it was an in-house work the job got boring as not much new and exciting was coming up, although it was well paying job and best part of it was laid back work culture, I decided to look for new a challenge. I wanted to get into a niche field in Penetration testing. Due to the advancements in framework oriented applications (built-in security) and tons of defensive products I feel few years down, traditional […]
Introduction Sometime back I was hunting for Vulnerabilities in Microsoft Web services, as Microsoft has large online infrastructure, finding a vulnerability which could lead to Microsoft hall of fame for security researchers wasn’t difficult. While browsing around their online services, one of their services, Microsoft hub translator caught my attention. Microsoft hub translator is and I quote: “Microsoft Translator Hub empowers businesses and communities to build, train, and deploy customized automatic language translation systems—-”. I signed up and started looking for vulnerabilities and found critical level vulnerability through which I was able to delete All Microsoft hub translator 13000+ projects. As the vulnerability is fixed now, I’m sharing […]
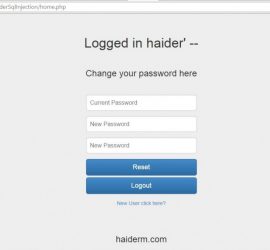
Introduction Second Order SQL injection is an application security vulnerability, it occurs when user-submitted values are stored in the database, and then it gets used by some other functionality in the application without escaping or filtering the data. Usually, data from external sources (user supplied) is considered dangerous and is escaped/filtered. Developers trust the data coming from the database. This behavior is similar to a Stored Cross Site Scripting attack. Second Order SQL Injection requires more knowledge of how submitted values are later used in order to perform successfully second-order SQL injection. Still confused? follow the example below:- Second Order […]