Which THREAT modelling framework/methodology should I go for?
This is a very common question nowadays, since the “Shift-left revolution”, we have all been trying to introduce security as early into the SDLC as possible (if we aren’t? we should!). THREAT modelling is the foundational activity of shifting left, which basically means finding threats early into the SDLC. Finding threats early in the software development lifecycle helps you save costs in terms of time, finances and more importantly possible reputational damage. Now that you are sold on doing threat modelling in the design phase of SDLC, the question you must be asking is which threat modelling framework/methodology should I use that best serves the cyber security and business objectives of my organization.
To answer this question we are going to look at STRIDE threat modelling methodology and DREAD threat modelling methodology, their possible use cases, and hopefully by going through the comparison you will get a good sense of which threat modelling framework you should use at which stage.
STRIDE | DREAD |
STRIDE is a Threat modelling framework that is used to Identity threats in the application architecture early when they are less costly to mitigate. As a result, it greatly reduces the total cost of development and improves the security posture of the application. STRIDE stands for:- - Spoofing (change state) - Tampering (Man in the middle, IDOR) | DREAD threat modelling is used to qualitatively measure the severity of each threat by asking a number of questions each carries a certain score, and the score is averaged out to find the severity of the vulnerability. DREAD stands for:- - Damage (how much damage attack can do?) |
STRIDE threat modelling is comparable to PASTA threat modelling methodology. PASTA stands for The Process for Attack Simulation and Threat Analysis, it is relatively a new threat modelling framework that is attacker centric and focuses on business impact analysis on aligning the business objectives with technology | DREAD threat modelling framework is comparable to CVSS, The Common Vulnerability Scoring System (CVSS) is a framework for measuring the severity of vulnerabilities. It is important to note that since CVSS is there to measure vulnerabilities, we cannot measure threats with CVSS because we do threat modelling on the design and architecture level. |
STRIDE threat modelling helps in categorizing identified threats into threat classes, this is particularly useful when you plan to mitigate entire classes of threats by using class specific controls rather than threat specific controls | DREAD threat modelling methodology helps in prioritizing threats by assigning a value to them, typically DREAD threat modelling performed on a threat would leave you with a value between 1 and 10. 10 would the threat that has the highest criticality and must be prioritized in mitigation and 1 would be least critical threat, generally an informational threat that can be accepted. |
STRIDE threat modelling framework is used to identify new threats that are in the design/architecture of the application. | DREAD threat modelling framework is used to qualitatively rank the already identified threats. This is useful to identify the priority of threats, i.e. which ones should be fixed first. |
DREAD threat modelling technique was also developed by Microsoft. | |
STRIDE threat modelling is performed on an architecture/design, typically a data flow diagram which has components, dataflow, external or internal entities etc. | DREAD threat modelling is performed on single threat that have already been identified (by using STRIDE or any other methodology) and DREAD helps in measuring the severity of the identified threat. |
STRIDE Threat modelling methodology cannot be customized, it has to be implemented as is, for example you cannot introduce new elements to STRIDE. The elements of STRIDE are Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Escalation of privileges. | DREAD can be modified by adding more customized questions and scoring criteria. If we take damage as an example we can add more criteria and score each of these as we like based on our internal practices within the organization and our risk appetite . |
Conclusion
Now that you have gone though the comparison of STRIDE and DREAD it must clear idea that these two threat modelling frameworks are entirely different from each other and serve a different purpose. One is to find and categorize the threats and another for measuring the severity of those threats. Both of these threat modelling methodologies can be used in a single threat model as well where STRIDE would help in finding and categorizing threats while DREAD could be used to measure the severity of those identified threats so they can be prioritized for mitigation. DREAD threat modelling technique can also be used for qualitatively measuring the a particular risk, however risk estimation has other techniques as well. STRIDE has different variations as well for example STRIDE per element, where each element of STRIDE is measured against the given architecture.

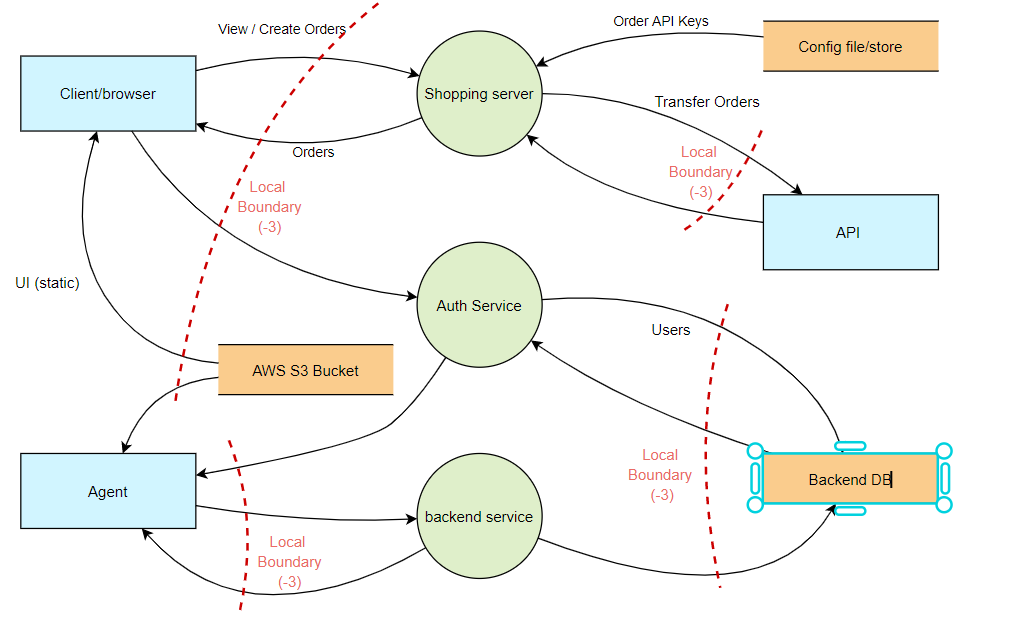

[…] Threat modelling is the process of identifying, analyzing, and mitigating potential security threats to a system or application. In the context of Amazon Simple Notification Service (SNS), potential threat scenarios could include unauthorized access to SNS topics and subscriptions, the use of SNS for spamming or phishing, and the use of SNS for denial of service (DoS) attacks. […]