Recently during a penetration testing assessment I was able to get Linux Privilege Escalation using weak NFS permissions in “/etc/exports”. Initially I got a restricted shell access with limited permissions by exploiting a vulnerable service. Started to recon for privilege escalation to root access but couldn’t get the “usual suspects” (Kernel Exploits, vulnerable services etc). Having no further progress for linux privilege escalation I went back to my pre-limitied shell recon results, its important to mention that penetration testers when they get the initial shell access often don’t look back at recon results and start gathering only the internal information about the target using the limited shell. I used to do the same but got lessons. Can’t stress enough to keep going back to all the information you gathered earlier, maybe you will find something interesting.
During the initial phase of recon I saw an NFS shared folder
didn’t pay much heed because it wasn’t a favorable candidate for initial shell access. The folder was empty as well, now that I had limited shell so took a peek at “/etc/exports” file. /etc/exports file contains configurations and permissions of which folders/file systems are exported to remote users.
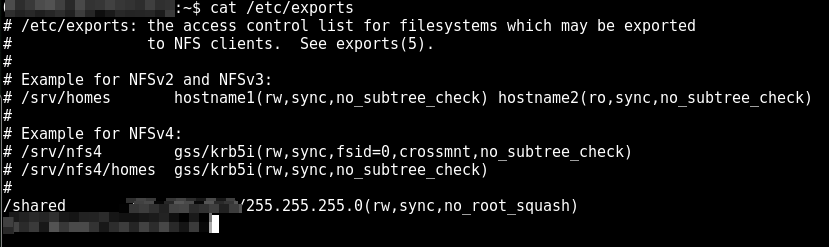
So we have “rw” (Read, write) , “sync” and note down the “no_root_squash” parameter and lets talk about what is Root Squashing.
NFS Root Squashing
Root Squashing parameter prevents having root access to remote root users connected to NFS volume. Remote root users are assigned a user “nfsnobody” when connected, which has the least local privileges. Alternatively “no_root_squash“ option turns off the “squashing of root user” and gives the remote user root access to the connected system (crazy right?). System administrators should always use “root_squash” parameter when configuring NFS drives to make sure remote root users are always “squashed”.
Now, firstly I copied a local shell on the /shared folder, if you feeling fancy, wget a reverse shell.
cp /bin/bash /shared
I mounted the NFS drive using the following command.
mount -t nfs server:/shared /mnt/
Now I have the access to /shared folder of remote system having bash shell in it. I changed the ownership and permissions of bash shell and set a SUID bit. When SUID bit is set on a file it allows any user to execute the file with the permission of the owner of the file rather than the permissions of the user who is executing the file.
chown root:root bash && chmod u+s bash
I get back to my limited shell user access on the victim server, all I had to do is to execute the bash shell in /shared folder and I’M THE KING!

if you use all_squash this does not work. I tested using latest version of NFS server on Ubuntu.
Yes because all_Squash option would squash every remote user including root.
[…] Linux Privilege Escalation using weak NFS permissions: t Linux Privilege Escalation using weak NFS permissions in “/etc/exports”. by Haider Mahmood […]