Introduction I have been doing Bug bounties for over 8 years now as a researcher on different platforms (Hackerone, Bugcrowd, Synack etc) but recently I had recent experience in bug bounties from the other side of the table, from the program side. After conducting the feature assessment and POCs of major platforms (an activity spanning over three months) I would like to share my experience which would hopefully help you choose the “right” platform to achieve your bounty objectives. This Bug Bounty Platform Comparison post focuses on why you need a bug bounty platform, criteria, and considerations in choosing the […]
Monthly Archives: August 2022
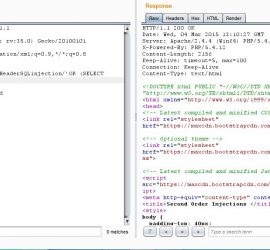
Introduction This post is the second in a series of noob-friendly posts that I am doing on SQL injection. Earlier I explained Second Order SQL Injections with Example. So in this post, I will be explaining the HTTP header Blind SQL injection, I prepared a Demo for the HTTP header Blind SQL injection For Example, HTTP has many reserved header fields the header I am choosing for the demonstration is the referrer header. What is HTTP Referrer Header? A referrer header is an HTTP header field, it’s simple job is to identify where the request originated from, for example, if […]
Introduction Organizations in today’s digital world hold data of their customers and clients which makes them a target for hackers, Organisations must follow robust cyber security policies/standards/guidelines to protect themselves, their employees, and most importantly their data against a wide range of threats. A Information security checklist helps organizations keep a track of their cyber security health to make sure an attacker cannot get unauthorized access to information that is stored on devices such as servers, databases, cloud, workstations, etc. Cyber incidents are on the rise, organisations are continuously attacked by threat actors that can range from lone wolfs to […]
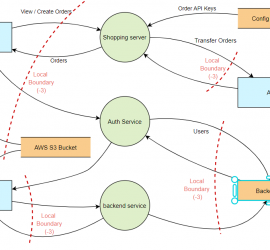
STRIDE Threat modelling Which THREAT modelling framework/methodology should I go for? This is a very common question nowadays, since the “Shift-left revolution”, we have all been trying to introduce security as early into the SDLC as possible (if we aren’t? we should!). THREAT modelling is the foundational activity of shifting left, which basically means finding threats early into the SDLC. Finding threats early in the software development lifecycle helps you save costs in terms of time, finances and more importantly possible reputational damage. Now that you are sold on doing threat modelling in the design phase of SDLC, the question […]