Its been 2 years and 8 months I was working as a Penetration tester looking after application security for the most part of my day. As it was an in-house work the job got boring as not much new and exciting was coming up, although it was well paying job and best part of it was laid back work culture, I decided to look for new a challenge. I wanted to get into a niche field in Penetration testing. Due to the advancements in framework oriented applications (built-in security) and tons of defensive products I feel few years down, traditional […]
Yearly Archives: 2018
Introduction Sometime back I was hunting for Vulnerabilities in Microsoft Web services, as Microsoft has large online infrastructure, finding a vulnerability which could lead to Microsoft hall of fame for security researchers wasn’t difficult. While browsing around their online services, one of their services, Microsoft hub translator caught my attention. Microsoft hub translator is and I quote: “Microsoft Translator Hub empowers businesses and communities to build, train, and deploy customized automatic language translation systems—-”. I signed up and started looking for vulnerabilities and found critical level vulnerability through which I was able to delete All Microsoft hub translator 13000+ projects. As the vulnerability is fixed now, I’m sharing […]
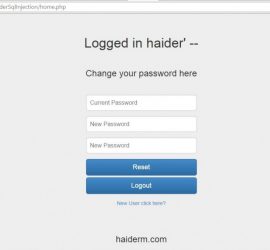
Introduction Second Order SQL injection is an application security vulnerability, it occurs when user-submitted values are stored in the database, and then it gets used by some other functionality in the application without escaping or filtering the data. Usually, data from external sources (user supplied) is considered dangerous and is escaped/filtered. Developers trust the data coming from the database. This behavior is similar to a Stored Cross Site Scripting attack. Second Order SQL Injection requires more knowledge of how submitted values are later used in order to perform successfully second-order SQL injection. Still confused? follow the example below:- Second Order […]
Couple of months back I saw a post on Linkedin about open roles for information security engineer at Google Zurich Switzerland office. I believe working for google (apart from perks they offer) is a privilege, you get to work with cutting edge technologies in a “comparatively stress free” environment (Check out Google’s offices you will know what I mean). Looking at the job responsibilities they seemed generic and short. Google keeps job responsibilities and required skills precise (Because of a reason explained later). This blog post is about my Google interview experience for information security engineer role. As you can guess, […]